SARS
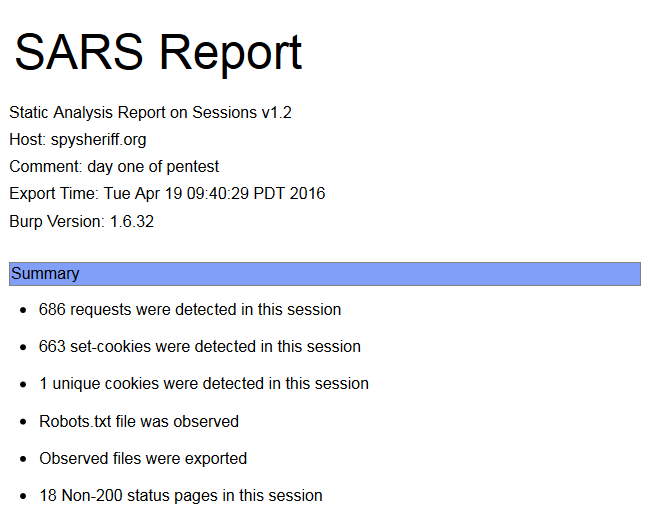
SARS - Static Analysis Report on Sessions
Summary
SARS is an offline static analysis web application penetration testing tool that uses the XML output from Burp Suite and performs a number of security checks to identify potential issues. SARS can also be used to enumerate a web application to gain information for further testing.
Features
Modules
- Session summary
- Regex searches
- Suspicious text searches
- Set-cookie analysis
- HTTPOnly flag
- Secure flag
- Request cookie analysis
- Unique cookies
- Base64 encoded cookie values
- Robots.txt
- Non-200 status pages
- Hidden form data
- HTTP header best practices
- Clickjacking protection
- POST requests
- Directory listing
- Request listing
Setup
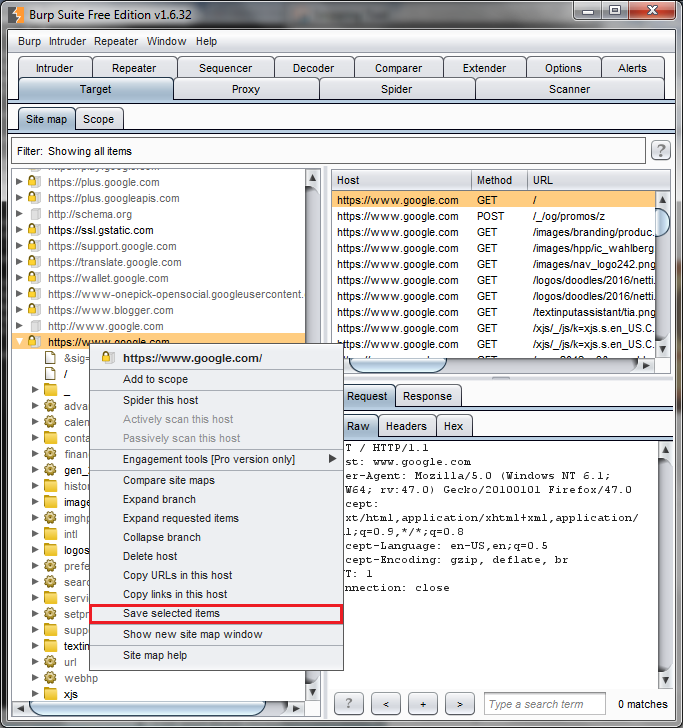
Exporting proxy data from Burp
Select the host from the sitemap that you want to export Right-click and select “Save Selected Items” In the pop-up save dialog box, make surre to uncheck the “Base64-enocde requests and responses box.
Usage
-c Comment to be added to the html file
-e Export all files by file type
-h Help file
-i Input xml file from Burp
-r Regex search term
Example
Usage:
1
C:\Users\Admin\SARS>python SARS.py -i SSOut -r \/.\/.\/. -e -c "day one of pentest"
Code
This post is licensed under CC BY 4.0 by the author.