D-CTF 2014 – Network 300
This was the Network 300 challenge from the recent D-CTF. Not many people solved this one and I got a lot of request for help in the IRC so I figured I would create write up for it.
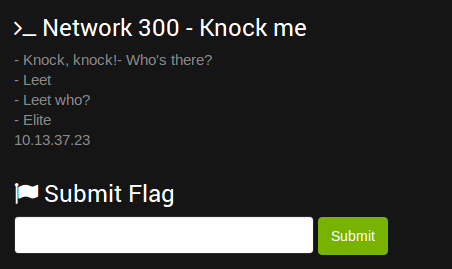
Reading the text in the challenge it was obvious that you would need to use port knocking to get through the firewall. It gives you two obvious ports to knock first: leet and elite (1337 and 31337).
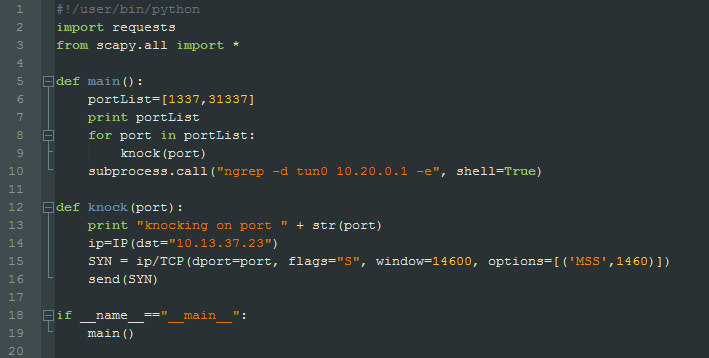
I wrote a python script to perform the port knocking on those two ports expecting to have a third port open up. I have seen this implementation of port knocking in the past. This took me some time as I tried different techniques such as port scanning the host as soon as the port knock was finished. this did not work.
Python code:
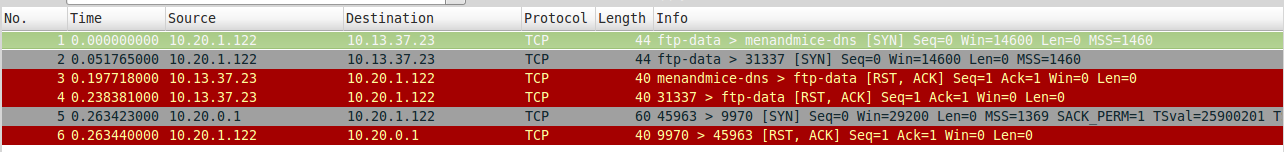
I fired up a packet capture to see what was taking place during the execution of the port knocking program I had written. What happens is that after the request on the second port is sent, we get a SYN back from 10.20.0.1 rather than the 10.13.37.23 that we were connecting to. Running the program a few times reveals that the dst port number on on this SYN packet is random. I obviously return the 0.1 address a RST ACK since I am no listening on that random port.
Since we need to complete that connection I need to open a listener on the port its trying to connect on. I ran the program a few times to see if there was any pattern that would make it obvious as to what port would be used next. I was unable to find a pattern so I would have to do things a little more manually.
From here there are two options, you can use IPTables to accept all incoming connections or you can create a second program that is multi-threaded and opens a listener on a group of ports. I tested both of these options and they both worked. For the multi-threaded option, I opened ncat listeners on a few hundred ports then ran the program a few times until we got a connection attempt on one of the ports that I was listening on.
Upon a connection the following is dumped to the terminal:
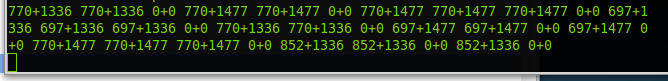
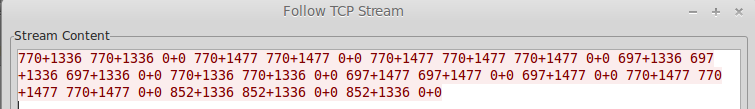
And in the TCP stream in Wireshark:
I was unsure what this was at first. This seemingly random addition did not make much sense. Luckily I recognized a few of the numbers as dual-tone multi-frequencies.
I looked up the frequency pairings and sure enough they were all dail pad numbers other than the 0+0.
Converting the multi-frequencies to numbers did not reveal a valid telephone number structure.
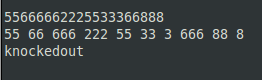
It took me a few minutes but its obvious that the numbers are not a telephone number but they are used in the old-school way of texting by pressing the same key multiple times to get to the letter you want.
Using this method and using the 0+0 as moving to the next character, it spells out the key.
Entering “knockedout” as the flag solves the challenge.
I was the 14th person to solve this one and it had several thousand attempts at the time I submitted the flag.